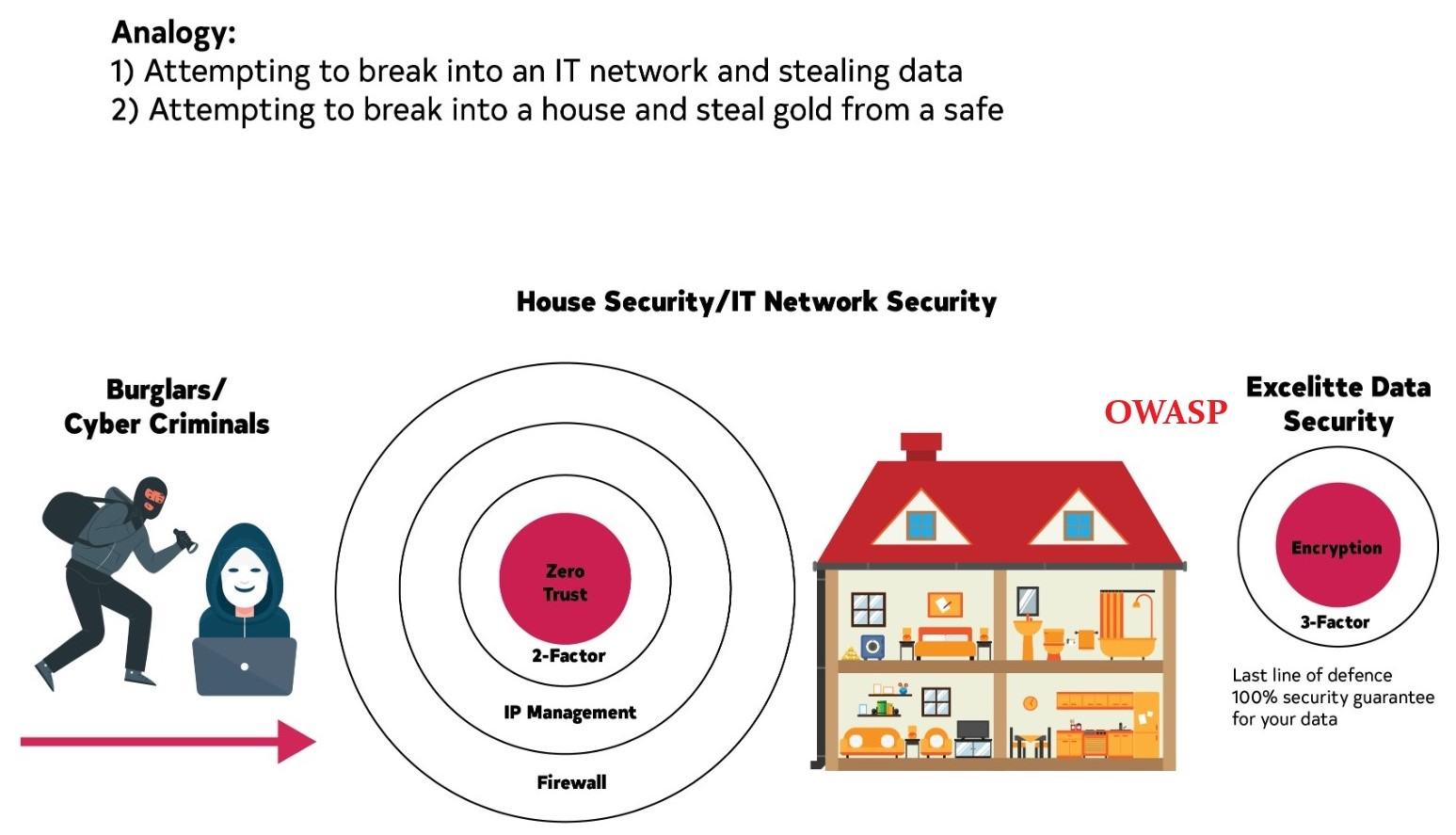
The Excelitte Cyber Security Digital Toolset consists of several cyber security software products and features to include:
- Excelitte Phishing Message Scanner - Scan Emails, Email Attachments & URL's link for all manner of security vulnerability.
- Excelitte Instant Data Capture from Spreadsheets - Automatic conversion or migration of your spreadsheet data to a more secure platform and stored as encrypted data.
- Excelitte Secure File Sharing - Store and share all files or data (text, image etc.) individually or across groups all held in an encrypted format.
- Excelitte Internet Cyber Security Web Browser - Combines the speed and usability of traditional browsers with advanced, enterprise-grade protection against data theft, ransomware, and cyber threats.
- Excelitte Web Crawler Chatbot - Crawls the web everyday capturing information on cyber criminals and use Open AI technology (like ChatGPT) to query and retrieve the information.
- Excelitte AI Robotic Penetration Tester - Software robot that automatically in seconds can conduct standardised black box cyber security testing.
Excelitte protects both individuals or organisations from both Email Phishing Message and SMS Phishing Message (Smishing) attacks, secures sensitive data/files from Cyber-Attacks.